Token Ring Network
By Stephen Bucaro
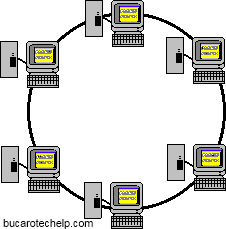
Token Ring technology was invented by IBM in 1984 and defined in standard IEEE 802.5
by the Institute of Electrical and Electronics Engineers. The token ring network has a
logical ring topology, and may be setup with a physical ring topology, but is usually
implemented in a physical star topology.
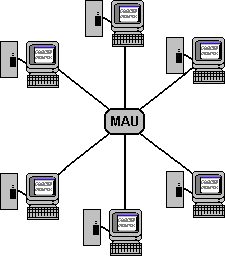
The central device of a token ring, called a Media Access Unit (MAU) or Multistation
Access Unit (MSAU), can be thought of as a "Ring in a Box". It allows multiple network
stations in a logical ring to connect as a physical star. The loop that used to
make up the ring is integrated into a chip.
In a physical Token ring topology, when a cable is open or a station is not operating,
the entire network goes down. However with a MAU, the broken circuit is shorted out,
closing the loop so the network can continue to operate and the nonoperating stations
may be unplugged without crashing the entire network.
Token ring protocol operates at the data link layer of the OSI model. In a token
ring network, the first computer to come online creates a three-byte data frame called
a token. The token is sent on the cable to the next node in the ring. The
token continues around the ring until it arrives at a node that wants to transmit data.
The node that wants to transmit data takes control of the token.
A node can only transmit data on the network cable when it takes control of the
token. Since only one token exists, only one node can transmit at a time. This prevents
the collisions that might occur with the Ethernet CSMA/CD access method.
After a node takes control of the token, it transmits a data packet. A Token Ring packet
contains four main parts: The data, the MAC address of the packetís source, the MAC address
of the packetís destination and a Frame Check Sequence (FCS) error checking code.
The data packet continues around the ring until it reaches the node with the
destination address. The receiving node accepts the data and marks the packet that the
data was received. The data packet then continues around the ring until it reaches the
source node again. The source node removes the packet from the cable and releases the
token so that another node may transmit.
Initially token ring ran at 4 Mbit/s, In 1989 IBM introduced the 16 Mbit/s token ring.
Other companies introduced proprietary 10 Mbit/s and 12 Mbit/s versions of token ring.
Speeds of 4 Mbit/s, 16 Mbit/s, 100 Mbit/s and 1 Gbit/s have been standardized by IEEE 802.5.
More Networking Topologies Articles:
• Data Center Management Best Practices
• Ethernet Network
• Ethernet Bridges
• A Guide to Broadband Internet Connections
• VPN (Virtual Private Network) headend or Concentrator
• Network Hubs
• The Secret of Maintaining Your Fiber Optic Network
• Technologies for the Internet of Things (IoT)
• Wireless or Wired Network?
• What Are Pseudo-Wires?
| 
