CISSP For Dummies, 6th Edition
Basic computer (system) architecture refers to the structure of a computer system and comprises its hardware, firmware, and software.
Hardware
Hardware consists of the physical components in computer architecture. The main components of the computer architecture include the CPU, memory, and bus.
CPU
The CPU (Central Processing Unit) or microprocessor is the electronic circuitry that performs a computer's arithmetic, logic, and computing functions. As shown in the figure, the main components of a CPU include
• Arithmetic Logic Unit (ALU): Performs numerical calculations and comparative logic functions, such as ADD, SUBTRACT, DIVIDE, and MULTIPLY.
• Bus Interface Unit (BIU): Supervises data transfers over the bus system between the CPU and I/O devices.
• Control Unit: Coordinates activities of the other CPU components during program execution.
• Decode Unit: Converts incoming instructions into individual CPU commands.
• Floating-Point Unit (FPU): Handles higher math operations for the ALU and control unit.
• Memory Management Unit (MMU): Handles addressing and cataloging data that's stored in memory and translates logical addressing into physical addressing.
• Pre-Fetch Unit: Preloads instructions into CPU registers.
• Protection Test Unit (PTU): Monitors all CPU functions to ensure that they're properly executed.
• Registers: Hold CPU data, addresses, and instructions temporarily, in special buffers.
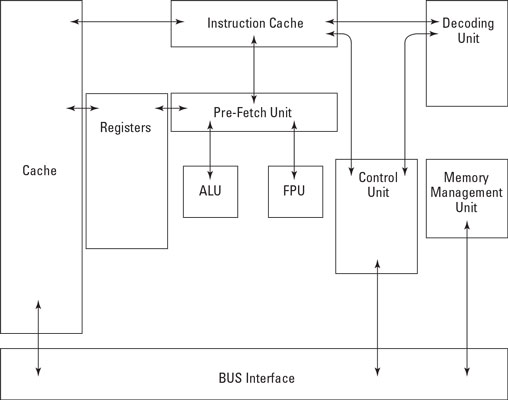
The main components of a CPU
The basic operation of a microprocessor consists of two distinct phases: fetch and execute. (It's not too different from what your dog does: You throw the stick, and he fetches the stick.) During the fetch phase, the CPU locates and retrieves a required instruction from memory. During the execute phase, the CPU decodes and executes the instruction. These two phases make up a basic machine cycle that's controlled by the CPU clock signals. Many complex instructions require more than a single machine cycle to execute.
The four operating states for a computer (CPU) are
• Operating (or run) state: The CPU executes an instruction or instructions.
• Problem (or application) state: The CPU calculates a solution to an application-based problem. During this state, only a limited subset of instructions (non-privileged instructions) is available.
• Supervisory state: The CPU executes a privileged instruction, meaning that instruction is available only to a system administrator or other authorized user/process.
• Wait state: The CPU hasn't yet completed execution of an instruction and must extend the cycle.
The two basic types of CPU designs used in modern computer systems are
• Complex-Instruction-Set Computing (CISC): Can perform multiple operations per single instruction. Optimized for systems in which the fetch phase is the longest part of the instruction execution cycle. CPUs that use CISC include Intel x86, PDP-11, and Motorola 68000.
• Reduced-Instruction-Set Computing (RISC): Uses fewer, simpler instructions than CISC architecture, requiring fewer clock cycles to execute. Optimized for systems in which the fetch and execute phases are approximately equal. CPUs that have RISC architecture include Alpha, PowerPC, and SPARC.
Microprocessors are also often described as scalar or superscalar. A scalar processor executes a single instruction at a time. A superscalar processor can execute multiple instructions concurrently.
Finally, many systems (microprocessors) are classified according to additional functionality (which must be supported by the installed operating system):
• Multitasking: Alternates the execution of multiple subprograms or tasks on a single processor.
• Multiprogramming: Alternates the execution of multiple programs on a single processor.
• Multiprocessing: Executes multiple programs on multiple processors simultaneously.
Two related concepts are multistate and multiuser systems that, more correctly, refer to operating system capabilities:
• Multistate: The operating system supports multiple operating states, such as single-user and multiuser modes in the UNIX/Linux world and Normal and Safe modes in the Windows world.
• Multiuser: The operating system can differentiate between users. For example, it provides different shell environments, profiles, or privilege levels for each user, as well as process isolation between users.
An important security issue in multiuser systems involves privileged accounts, and programs or processes that run in a privileged state. Programs such as su (UNIX/Linux) and RunAs (Windows) allow a user to switch to a different account, such as root or administrator, and execute privileged commands in this context. Many programs rely on privileged service accounts to function properly. Utilities such as IBM's Superzap, for example, are used to install fixes to the operating system or other applications.
Bus
The bus is a group of electronic conductors that interconnect the various components of the computer, transmitting signals, addresses, and data between these components. Bus structures are organized as follows:
• Data bus: Transmits data between the CPU, memory, and peripheral devices.
• Address bus: Transmits addresses of data and instructions between the CPU and memory.
• Control bus: Transmits control information (device status) between the CPU and other devices.
Main memory
• Main memory (also known as main storage) is the part of the computer that stores programs, instructions, and data. The two basic types of physical (or real — as opposed to virtual — more on that later) memory are
• Random Access Memory (RAM): Volatile memory (data is lost if power is removed) is memory that can be directly addressed and whose stored data can be altered. RAM is typically implemented in a computer's architecture as cache memory and primary memory. The two main types of RAM are
• Dynamic RAM (DRAM): Must be refreshed (the contents rewritten) every two milliseconds because of capacitance decay. Refreshing is accomplished by using multiple clock signals known as multiphase clock signals.
• Static RAM (SRAM): Faster than DRAM and uses circuit latches to represent data, so it doesn't need to be refreshed. Because SRAM doesn't need to be refreshed, a single-phase clock signal is used.
• Read-Only Memory (ROM): Nonvolatile memory (data is retained, even if power is removed) is memory that can be directly addressed but whose stored data can't be easily altered. ROM is typically implemented in a computer's architecture as firmware (which we discuss in the following section). Variations of ROM include
• Programmable Read-Only Memory (PROM): This type of ROM can't be rewritten.
• Erasable Programmable Read-Only Memory (EPROM): This type of ROM is erased by shining ultraviolet light into the small window on the top of the chip. (No, we aren't kidding.)
• Electrically Erasable Programmable Read-Only Memory (EEPROM): This type of ROM was one of the first that could be changed without UV light. Also known as Electrically Alterable Read-Only Memory (EAROM).
• Flash Memory: This type of memory is used in USB thumb drives.
[ Remember: Be sure you don't confuse the term “main storage” with the storage provided by hard drives.]
Secondary Memory
Secondary memory (also known as secondary storage) is a variation of these two basic types of physical memory. It provides dynamic storage on nonvolatile magnetic media such as hard drives, solid-state drives, or tape drives (which are considered sequential memory because data can't be directly accessed — instead, you must search from the beginning of the tape). Virtual memory (such as a paging file, swap space, or swap partition) is a type of secondary memory that uses both installed physical memory and available hard-drive space to present a larger apparent memory space to the CPU than actually exists in main storage.
Two important security concepts associated with memory are the protection domain (also called protected memory) and memory addressing.
A protection domain prevents other programs or processes from accessing and modifying the contents of address space that's already been assigned to another active program or process. This protection can be performed by the operating system or implemented in hardware. The purpose of a protection domain is to protect the memory space assigned to a process so that no other process can read from the space or alter it. The memory space occupied by each process can be considered private.
Memory space describes the amount of physical memory available in a computer system (for example, 2 GB), whereas address space specifies where memory is located in a computer system (a memory address). Memory addressing describes the method used by the CPU to access the contents of memory. A physical memory address is a hard-coded address assigned to physically installed memory. It can only be accessed by the operating system that maps physical addresses to virtual addresses. A virtual (or symbolic) memory address is the address used by applications (and programmers) to specify a desired location in memory. Common virtual memory addressing modes include
• Base addressing: An address used as the origin for calculating other addresses.
• Absolute addressing: An address that identifies a location without reference to a base address — or it may be a base address itself.
• Indexed addressing: Specifies an address relative to an index register. (If the index register changes, the resulting memory location changes.)
• Indirect addressing: The specified address contains the address to the final desired location in memory.
• Direct addressing: Specifies the address of the final desired memory location.
[ Remember: Don't confuse the concepts of virtual memory and virtual addressing. Virtual memory combines physical memory and hard drive space to create more apparent memory (or memory space). Virtual addressing is the method used by applications and programmers to specify a desired location in physical memory.]
Firmware
Firmware is a program or set of computer instructions stored in the physical circuitry of ROM memory. These types of programs are typically changed infrequently or not at all. In servers and user workstations, firmware usually stores the initial computer instructions that are executed when the server or workstation is powered on; the firmware starts the CPU and other onboard chips, and establishes communications by using the keyboard, monitor, network adaptor, and hard drive. The firmware retrieves blocks of data from the hard drive that are then used to load and start the operating system.
A computer's BIOS is a common example of firmware. BIOS, or Basic Input-Output System, contains instructions needed to start a computer when it's first powered on, initialize devices, and load the operating system from secondary storage (such as a hard drive).
Firmware is also found in devices such as smartphones, tablets, DSL/cable modems, and practically every other type of Internet-connected device, such as automobiles, thermostats, and even your refrigerator.
Firmware is typically stored on one or more ROM chips on a computer's motherboard (the main circuit board containing the CPU(s), memory, and other circuitry).
Software
Software includes the operating system and programs or applications that are installed on a computer system.
Operating Systems
A computer operating system (OS) is the software that controls the workings of a computer, enabling the computer to be used. The operating system can be thought of as a logical platform, through which other programs can be run to perform work.
The main components of an operating system are
• Kernel: The core component of the operating system that allows processes, control of hardware devices, and communications to external devices and systems to run.
• Device drivers: Software modules used by the kernel to communicate with internal and external devices that may be connected to the computer.
• Tools: Independent programs that perform specific maintenance functions, such as filesystem repair or network testing. Tools can be run automatically or manually.
The operating system controls a computer's resources. The main functions of the operating system are
• Process management: Sets up an environment in which multiple independent processes (programs) can run.
• Resource management: Controls access to all available resources, using schemes that may be based on priority or efficiency.
• I/O device management: Controls communication to all devices that are connected to the computer, including hard drives, printers, monitors, keyboard, mouse, and so on.
• Memory management: Controls the allocation and access to main memory (RAM), allocating it to processes, as well as general uses such as disk caching.
• File management: Controls the file systems that are present on hard drives and other types of devices and performs all file operations on behalf of individual processes.
• Communications management: Controls communications on all available communications media on behalf of processes.
Virtualization
A virtual machine is a software implementation of a computer, enabling many running copies of an operating system to execute on a single running computer without interfering with each other. Virtual machines are typically controlled by a hypervisor, a software program that allocates resources for each resident operating system (called a guest).
A hypervisor serves as an operating system for multiple operating systems. One of the strengths of virtualization is that the resident operating system has little or no awareness of the fact that it's running as a guest — instead, it may believe that it has direct control of the computer's hardware. Only your system administrator knows for sure.
Containerization
A container is a lightweight, standalone executable package of a piece of software that includes everything it needs to run. A container is essentially a bare-bones virtual machine that only has the minimum software installed necessary to deploy a given application. Popular container platforms include Docker and Kubernetes.
About the Book Author
Lawrence Miller, CISSP, is a security consultant with experience in consulting, defense, legal, nonprofit, retail, and telecommunications. Peter Gregory, CISSP, is a CISO and an executive security advisor with experience in SaaS, retail, telecommunications, nonprofit, legalized gaming, manufacturing, consulting, healthcare, and local government.
Secure your CISSP certification!
If you're a security professional seeking your CISSP certification, this book is a perfect way to prepare for the exam. Covering in detail all eight domains, the expert advice inside gives you the key information you'll need to pass the exam. Plus, you'll get tips on setting up a 60-day study plan, tips for exam day, and access to an online test bank of questions.
CISSP For Dummies is fully updated and reorganized to reflect upcoming changes (ISC)2 has made to the Common Body of Knowledge. Complete with access to an online test bank this book is the secret weapon you need to pass the exam and gain certification.
• Get key information for all eight exam domains
• Find test-taking and exam-day tips and tricks
• Benefit from access to free online practice questions and flash cards
• Prepare for the CISSP certification in 2018 and beyond
You've put in the time as a security professional—and now you can reach your long-term goal of CISSP certification.
Reader A. Dorman says, "It took me about 8 hours to read and totally take in. This is the only CISSP book I didn't fall asleep reading. Shon Harris's book, I passed out on. ISC2's book, passed out on. This book was written in a way that doesn't make one fall asleep reading. The information is there but not to the extent of Shon Harris by any means. I would recommend reading this AND another book. This alone will not get you to where you need to be. I passed May 14 2019, so I can tell you that you will not pass only reading this.
More Computer Architecture Articles:
• Round-Robin CPU Scheduling Algorithm
• Multilevel Queue CPU Scheduling Algorithm
• Difference between Stack, Heap, and Queue
• Load Balancing Multiple CPUs in Symmetric Multiprocessing
• Microcontroller Registers
• How Computer Memory Works
• Dynamic Loading of Program Routines and Dynamically linked libraries (DLLs)
• Operating System Memory Protection in a Paged Environment
• Multicore Programming
• Capacitors in AC Circuits



